In today's digital landscape, the quality of your survey data directly impacts the reliability of your insights and, ultimately, your reputation. dtect's comprehensive security features work together to protect your surveys from fraudulent responses before they can compromise your data, allowing your team to focus on driving reliable insights rather than cleaning bad data.
The most effective security strategy often combines multiple features while considering your specific research needs and audience characteristics.
Security Features
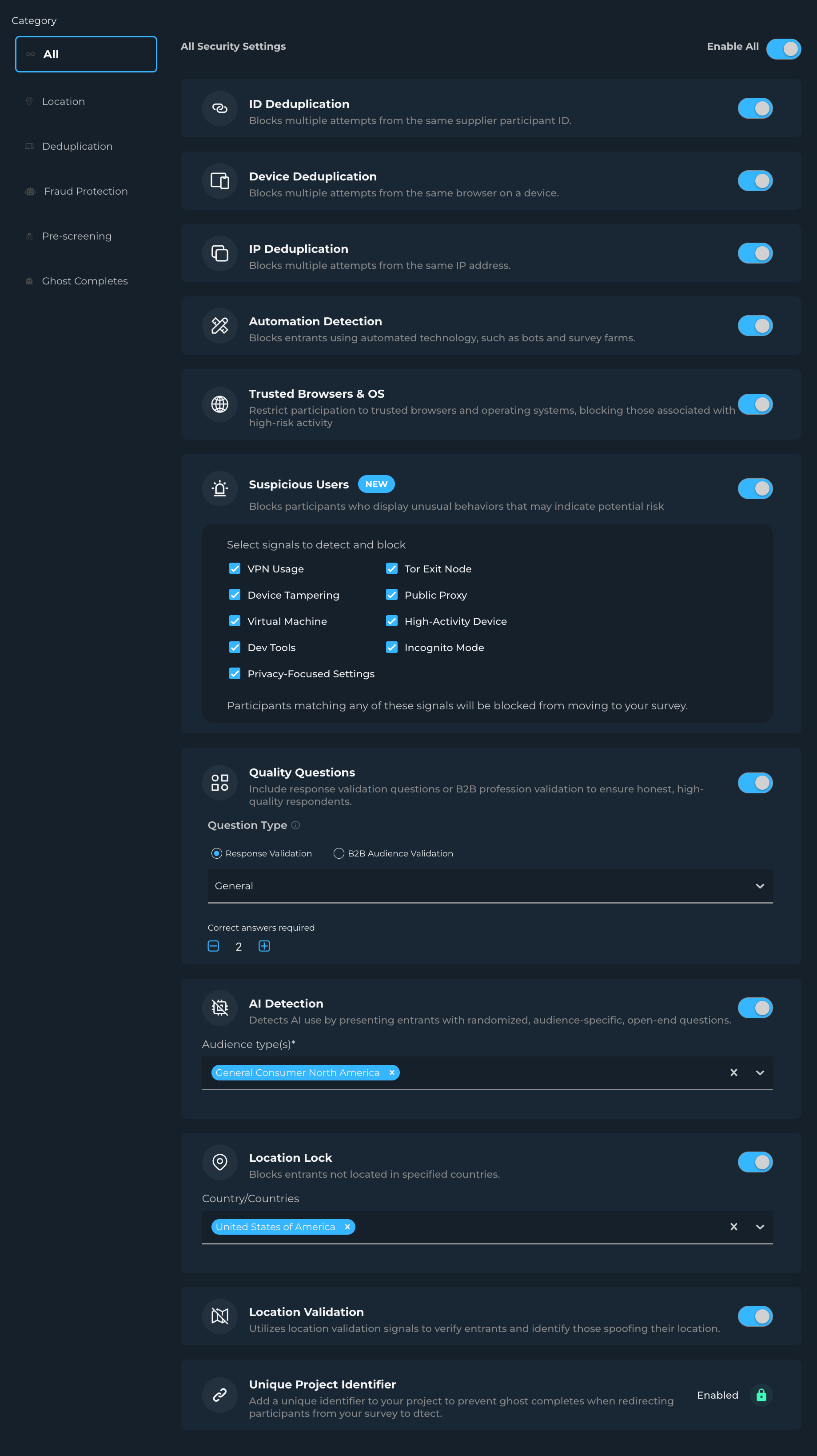
Deduplication
ID Deduplication: Prevents multiple submissions from the same participant ID.
Device Deduplication: Prevents multiple submissions from the same device, ensuring each response represents a unique participant.
IP Deduplication: Identifies and blocks multiple responses from the same network location, maintaining response diversity.
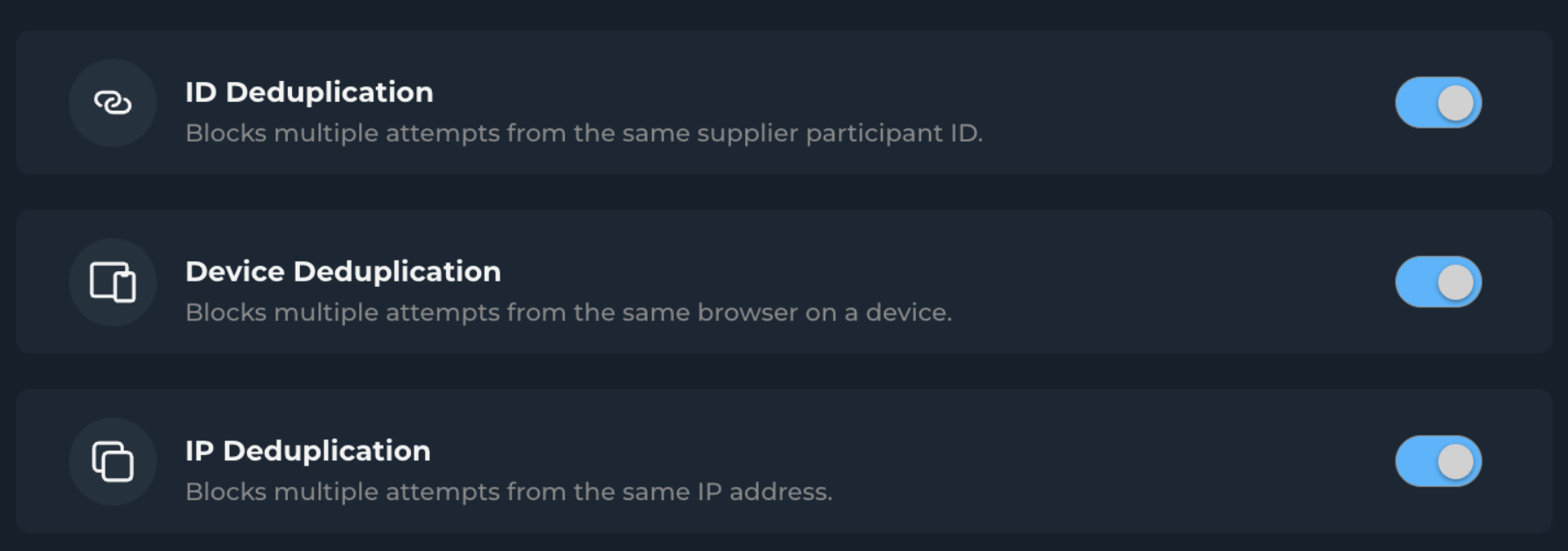
Location Security
Location Validation: Verifies participant location authenticity through sophisticated validation techniques, including VPN detection.
Location Lock: Ensures participants are physically located in your target countries, maintaining geographical relevance.
ℹ️ What is a VPN?
A Virtual Private Network (VPN) allows users to mask their true location by routing their internet connection through servers in different locations. While VPNs have legitimate uses, they can also be used to circumvent geographic restrictions in surveys.
Automated Threat Detection
Automation Detection: Provides protection against bots and automated responses while maintaining genuine participant access.
Suspicious Users: Blocks participants flagged for abnormal device or browser characteristics.
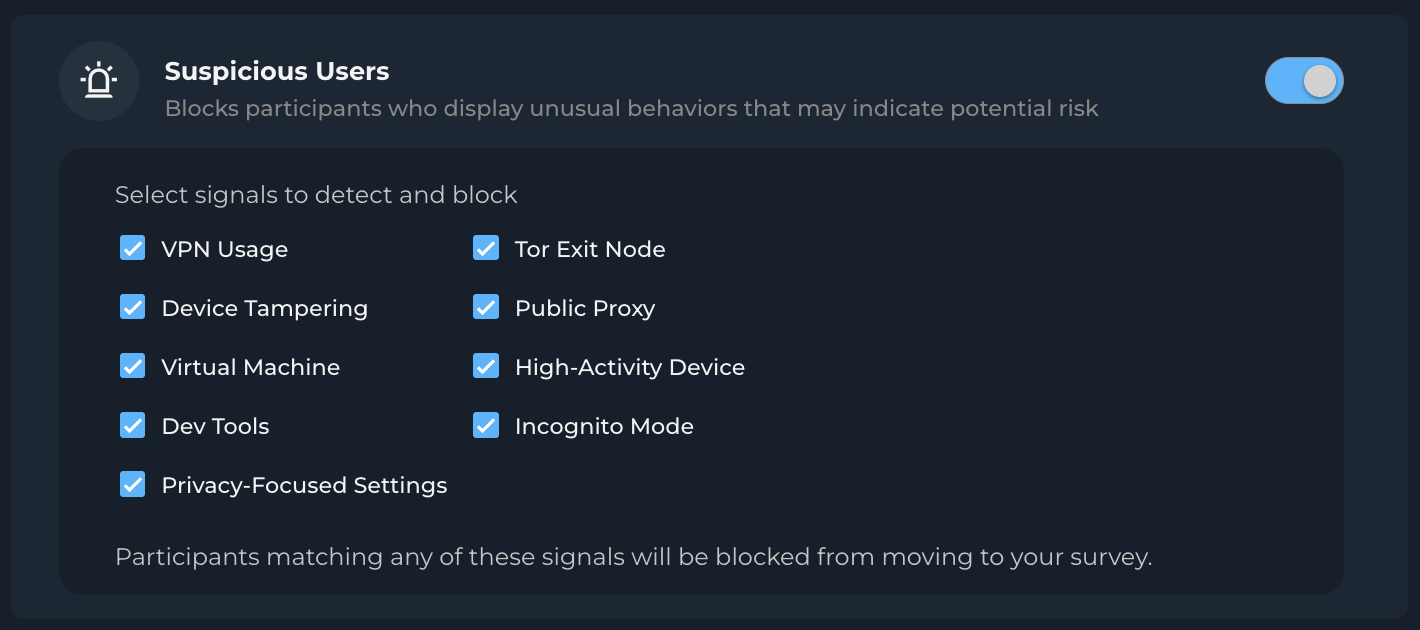
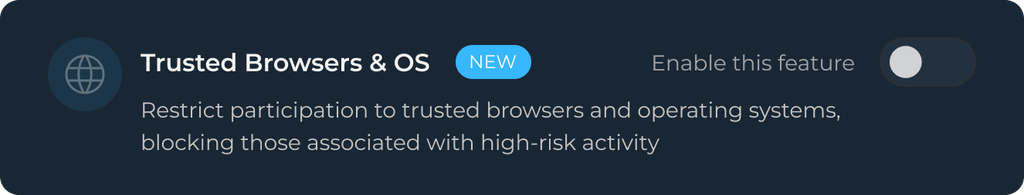
Trusted Brosers & OS: Restrict participation to trusted browsers and operating systems, blocking those associated with high-risk activity.
Pre-screening
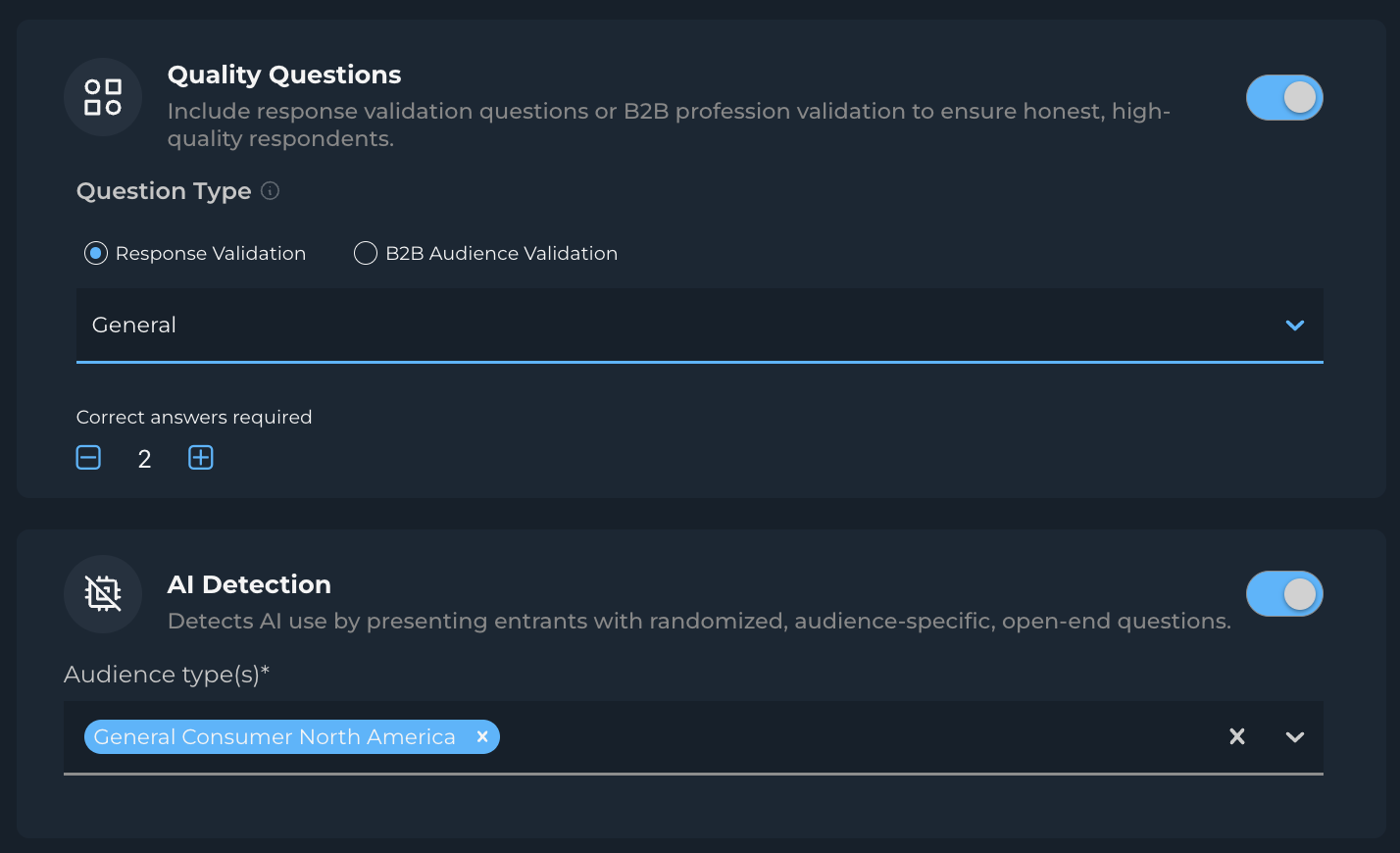
Quality Questions: Verifies participant qualifications through randomized, closed-ended questions. This ensures the authenticity, attention, and qualification of survey participants.
AI Detection: Identifies potential AI-generated responses to maintain authentic human participation.
Implementation Best
Balancing Security and Accessibility
While implementing multiple security features provides the strongest protection, consider your study's specific needs:
- High-stakes research may benefit from enabling all security features
- Consider selective feature activation for studies requiring broader accessibility
- Monitor and adjust security settings based on response rates and data quality
Implementing all security features provides maximum protection but may result in lower incidence rates. Consider your study requirements when choosing which features to enable.
Common Implementation Scenarios
- High-Security Studies
- Enable all security features
- Set stricter Automation Detection thresholds
- Ideal for high-value B2B research
- Consumer Studies
- Focus on core security features
- Adjust thresholds to maintain accessibility
- Balance between security and completion rates
- International Studies
- Emphasize Location Validation
- Configure Location Lock for target regions
- Consider language and cultural factors
Troubleshooting
General Guidelines
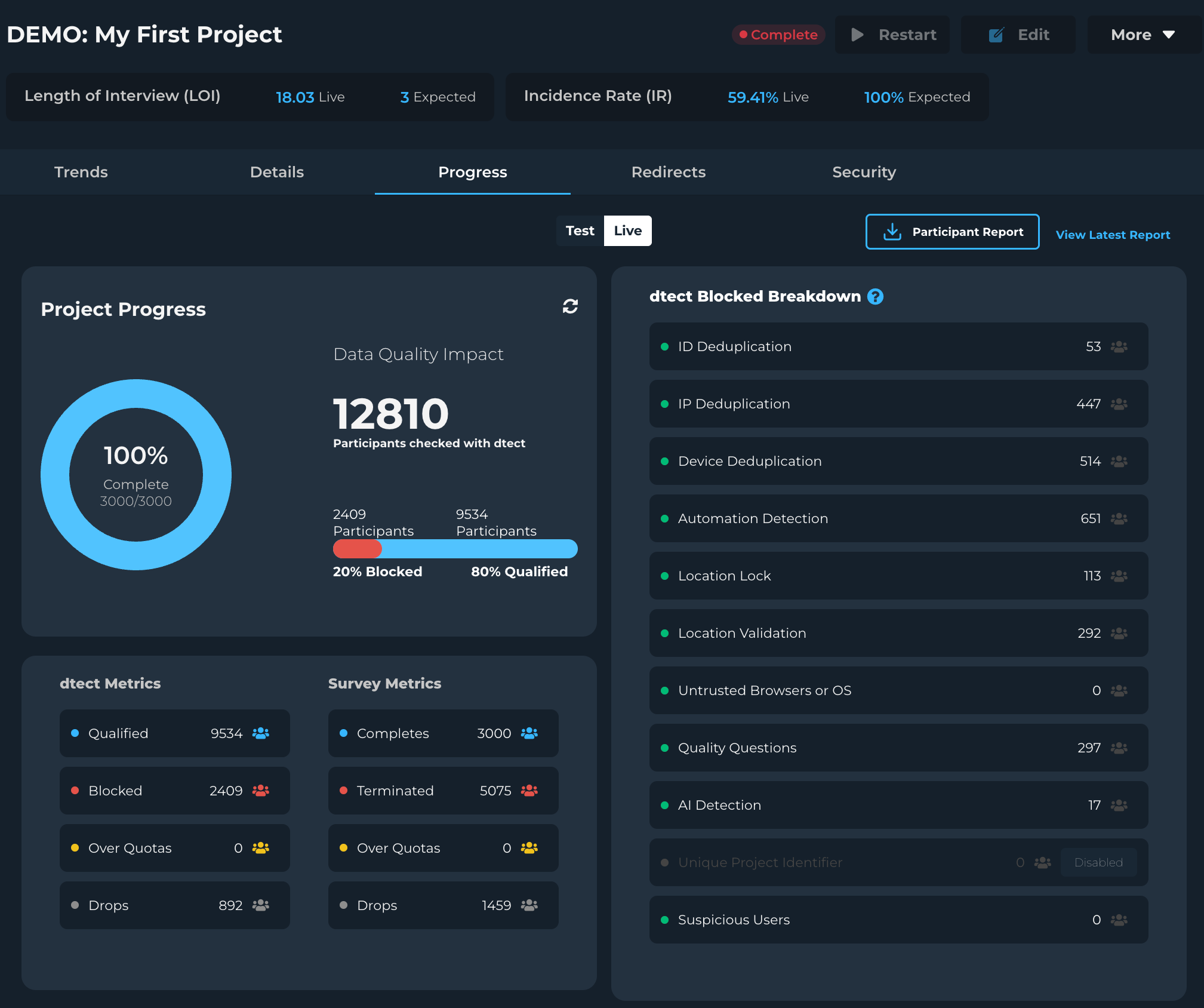
- Review the Progress page for detailed security metrics
- Monitor termination rates across different security features
- Adjust settings if experiencing unexpected participant blocking
Regular review of your Progress page helps identify potential issues before they significantly impact your study.
Common Scenarios
- High Security Termination Rates
- Review security thresholds
- Check for legitimate regional access patterns
- Verify supplier traffic quality
- Unexpected Terminations
- Confirm Location Lock settings match target regions
- Review Audience Validation configuration
- Check for potential VPN-related issues
- Response Rate Issues
- Balance security settings with accessibility
- Review and adjust feature combinations
- Consider your target audience characteristics
Need Additional Help?
Contact your Customer Success Manager for:
- Feature optimization recommendations
- Specific security configuration guidance
- Detailed information about feature capabilities
Remember: The goal is to maintain high data quality while ensuring legitimate participants can successfully complete your surveys. Regular monitoring and adjustment of security settings helps achieve this balance.